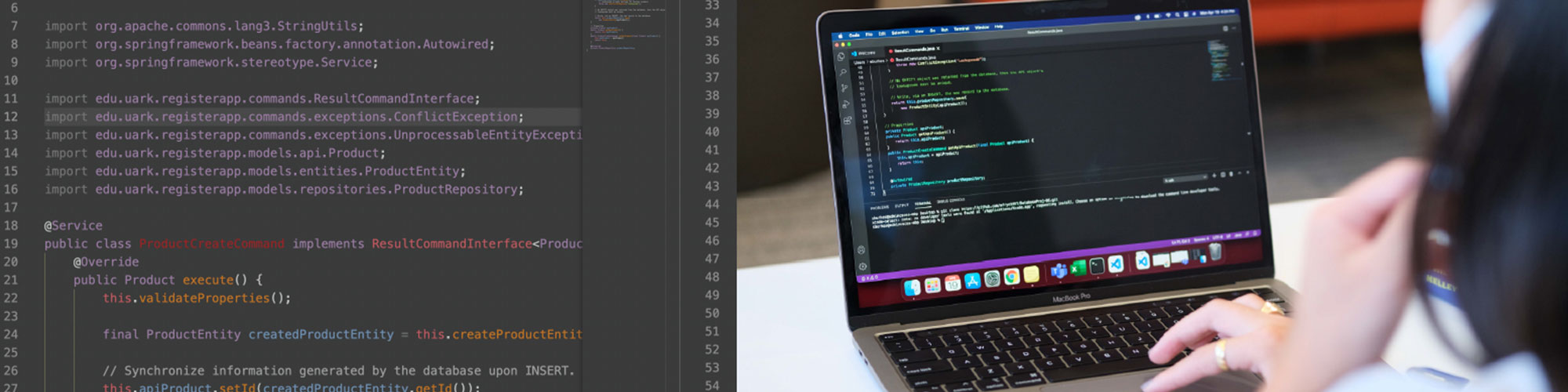
What is Computer Engineering?
Computer engineers deal with both software and hardware. As a computer engineer, you could design entire computer systems and networks, making sure that the hardware, or physical equipment, is capable of running the appropriate software. You might build devices such as retinal scanners that identify people by checking their eyes, or you could design computers that are incorporated into prosthetic devices to aide people with disabilities. Those who continue onward to obtain a graduate degree in either computer science or computer engineering learn to advance the frontiers of science. With an MS or PhD, you will invent the new technologies that enable the next generation of software and computing devices.
What is Computer Science?
Computer scientists specialize in the software side of computing, focusing on writing new programs that allow computer applications to run faster and more efficiently. You might work for a security company, creating technology that reduces the risks of viruses and hackers, or develop flight simulation exercises that allow airline pilots to practice managing flight problems. Those who continue onward to obtain a graduate degree in either computer science or computer engineering learn to advance the frontiers of science. With an MS or PhD, you will invent the new technologies that enable the next generation of software and computing devices.
$71K
AVERAGE CSCE STARTING SALARY
AI
TECHNOLOGY COURSES
Hands-on experience
WITH LEADING RESEARCHERS
CYBER-
SECURITY
GRADUATE CERTIFICATE
MOBILE
APP
DEVELOPMENT COURSES
Quick Links
Faculty & Staff
Faculty and staff resources
can be found here.
News
Get your
current news stories!
Tech Support
IT Help
(Campus VPN Required)
Feedback
Please leave your
anonymous comment.


